Automated Process to create IaC pipeline with Security
Using the CloudFormation Template to build the IaC pipeline in you AWS account
Here is the link to the GitHub Repository with the CloudFormation template to build the IaC architecture into your AWS account -> GitHub Repository

Let’s build the CloudFormation template:
Create Stack
1. Click on the button below to deploy the stack in AWS CloudFormation
Make sure you are using the us-east-1 in AWS. If you are using a different region to deploy the CloudFormation template, please use the proper Image ID from the region that you are using. This CloudFormation template has some dependencies with us-east-1.
If you want to download the CloudFormation Template content click on the link here
2. On this page click on the Next button
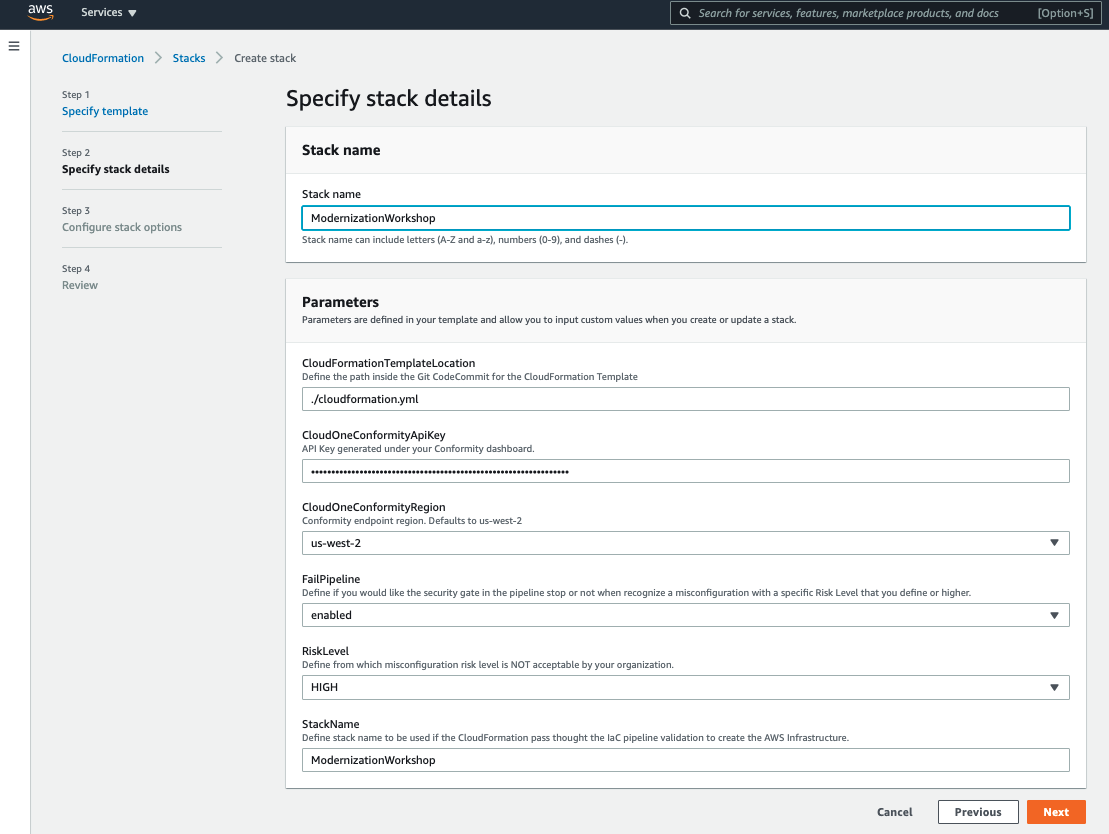
3. Most of the parameters are pre-configured already, but you still need to define the Stack name and the Cloud One - Conformity API Key.
-
Stack name:
ModernizationWorkshop -
Cloud One - API Key: Check out Creating API Key for an explanation on how to get the API Key in the Cloud One Console through User Management.
After filling up the two fields missing information click Next
4. Click Next again
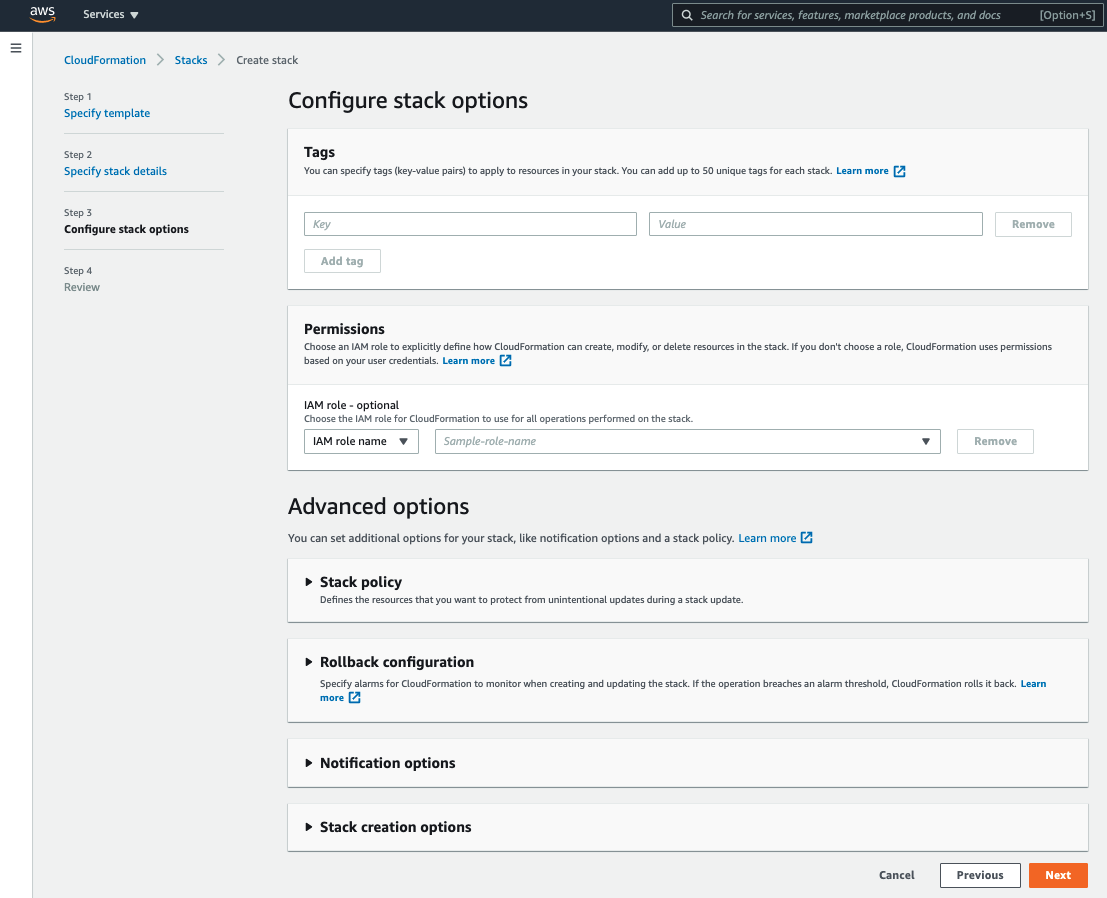
5. After, you will need to scroll down to acknowledge that AWS will be creating an AWS Identity and Access Management (IAM) resource for the roles and policies needed for the lab. Next, click on Create stack
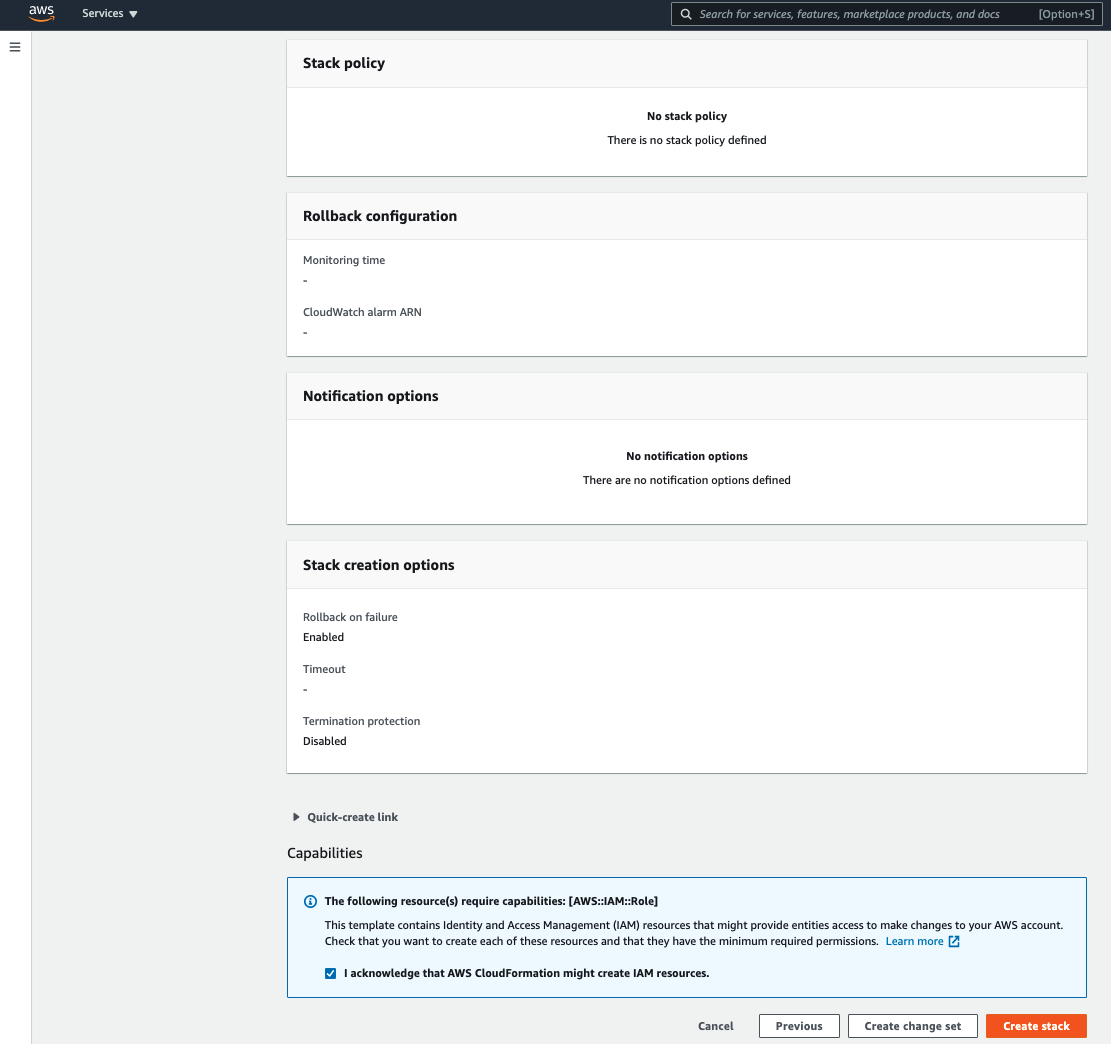
6. After creating the stack, you will be able to play with the CloudFormation example in the CodeCommit repository.
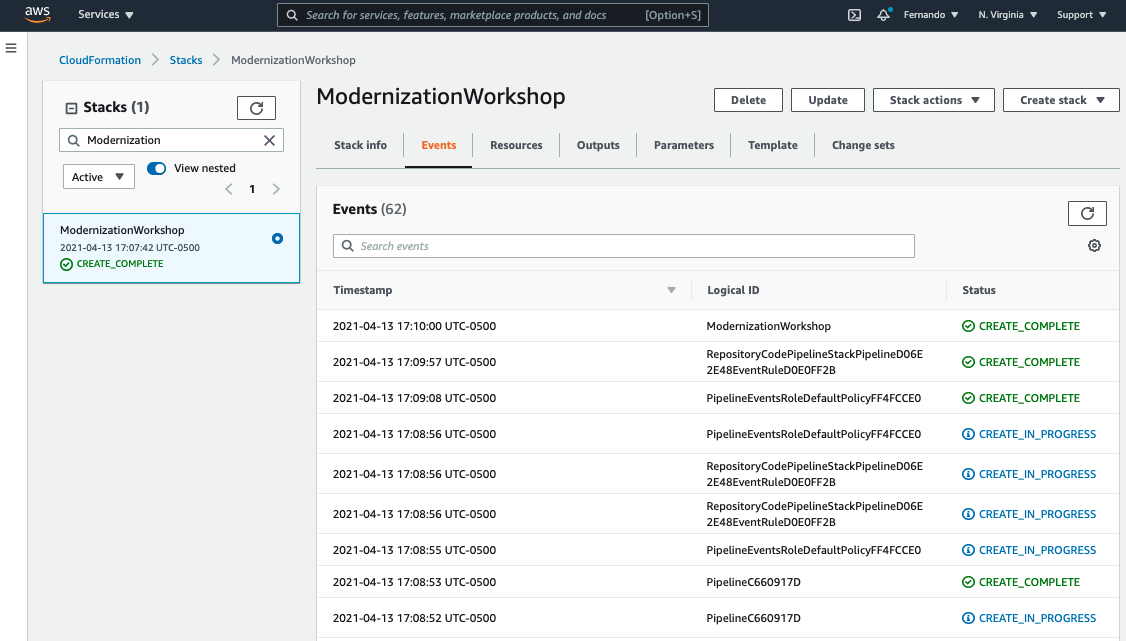
7. Now, let’s see how the first IaC pipeline execution goes with the CloudFormation example that you will have in the CodeCommit.
- Search for CodePipeline on AWS console
- Click on the icon, and you will see a pipeline failed like the image below.
- Then click on the Pipeline Name
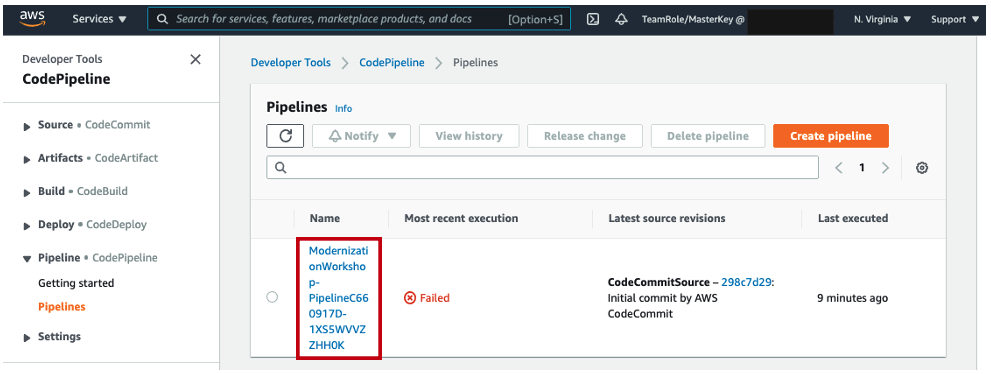
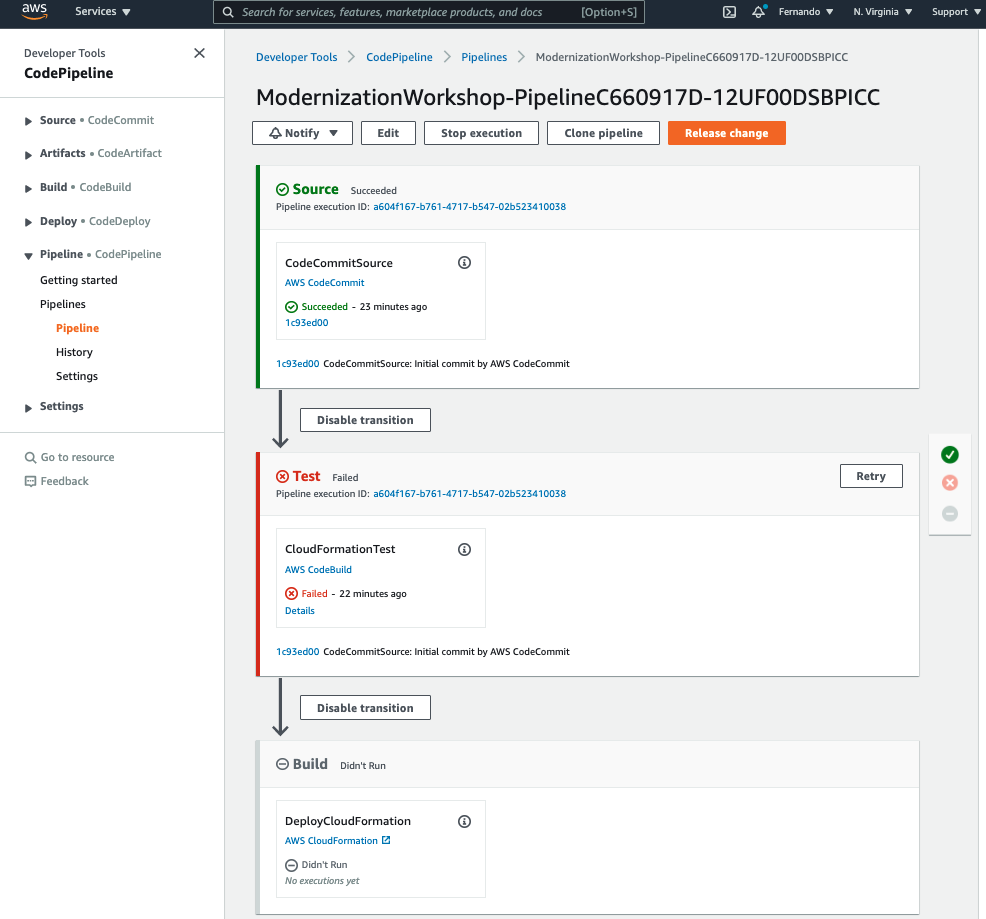
8. The first release that automatically kicked-off failed. To see more details, click Details on the Test stage, then click Link to Execution.
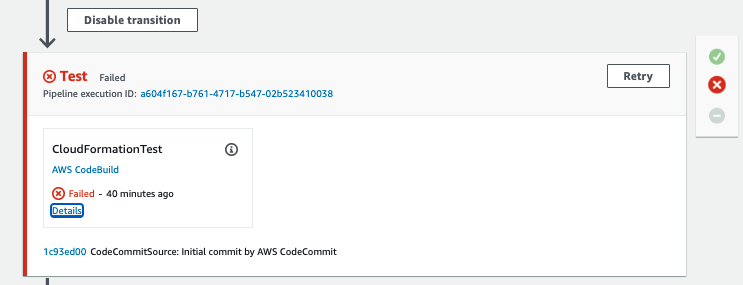
9. Conformity has generated findings as an artifiact for the failed build, you will see more information about the build stage of the template scanner following the steps below:
- Click the Build details tab, scroll down to Artifacts
- After click the artifact link that was uploaded to the Amazon Simple Storage Service (S3) bucket.
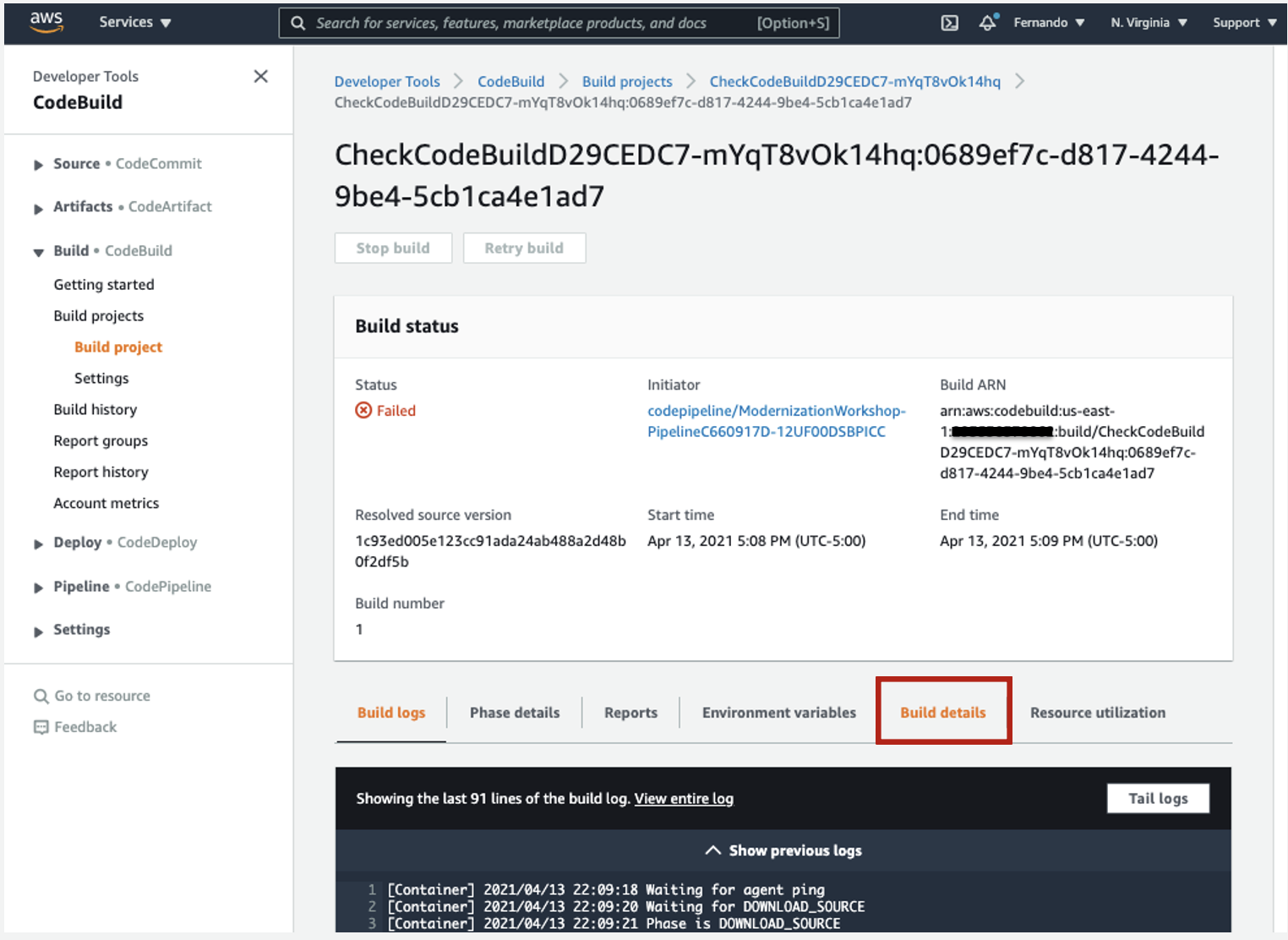
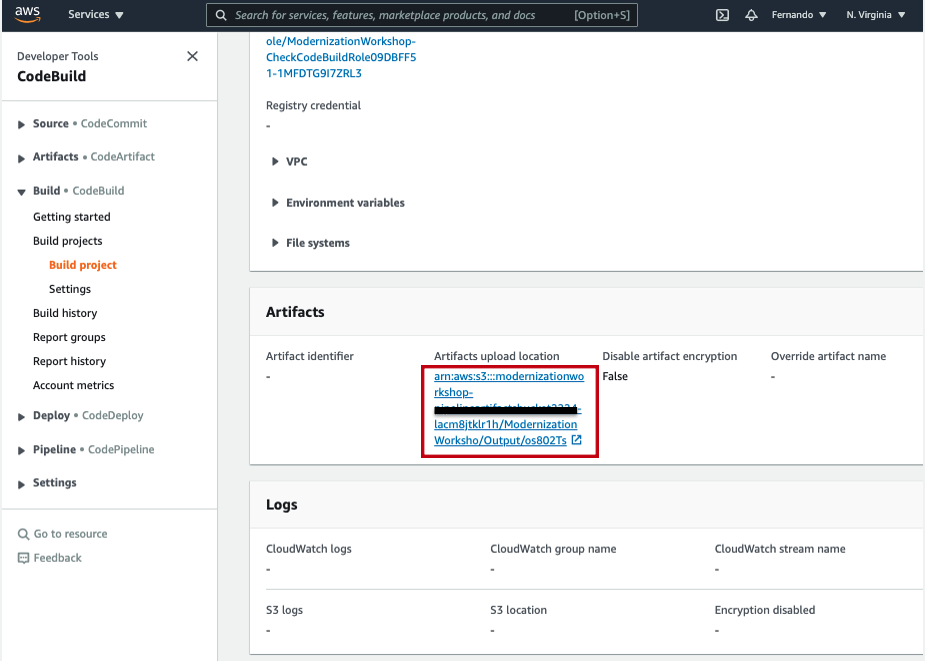
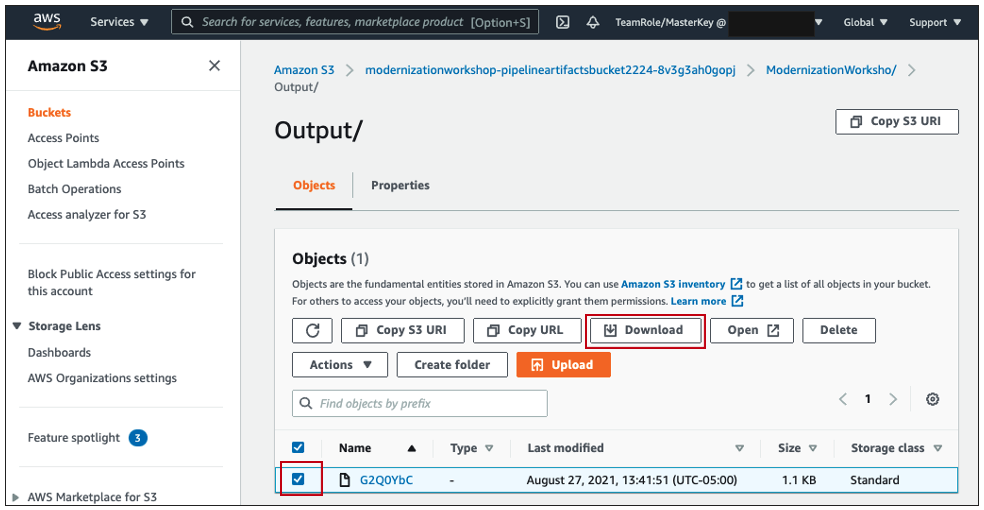
10. You can download the latest file to see the results by selecting the artifact and click in the button Download. You will need to unzip the file and you will see the following information as a JSON format:
If the file downloaded doesn't have the zip extension, please add .zip to the file and unzip it.
INFO: Obtaining required environment variables...
INFO: All environment variables were received. The pipeline will fail if any "HIGH" level issues are found
INFO: Offending entries:
[
{
"attributes": {
"categories": [
"security"
],
"compliances": [
"GDPR",
"AWAF",
"NIST4",
"NIST5",
"NIST-CSF",
"ISO27001",
"HIPAA",
"HITRUST",
"PCI",
"APRA",
"FEDRAMP",
"MAS",
"CSA"
],
"cost": 0,
"descriptorType": "s3-bucket",
"ignored": false,
"last-updated-date": null,
"logicalResourceId": "S3Bucket",
"message": "Bucket S3Bucket does not enforce Server-Side Encryption",
"not-scored": false,
"pretty-risk-level": "High",
"provider": "aws",
"region": "us-east-1",
"resolution-page-url": "https://www.cloudconformity.com/knowledge-base/aws/S3/server-side-encryption.html",
"resource": "S3Bucket",
"risk-level": "HIGH",
"rule-title": "Server Side Encryption",
"status": "FAILURE",
"tags": [
"Environment::ModernizationWorkshop"
],
"waste": 0
},
"id": "ccc:OrganisationId:S3-016:S3:us-east-1:S3Bucket",
"relationships": {
"account": {
"data": null
},
"rule": {
"data": {
"id": "S3-016",
"type": "rules"
}
}
},
"type": "checks"
},
{
"attributes": {
"categories": [
"security"
],
"compliances": [
"GDPR",
"AWAF",
"NIST4",
"NIST5",
"NIST-CSF",
"ISO27001",
"HIPAA",
"HITRUST",
"ASAE-3150",
"PCI",
"APRA",
"FEDRAMP",
"MAS",
"CSA"
],
"cost": 0,
"descriptorType": "s3-bucket",
"ignored": false,
"last-updated-date": null,
"logicalResourceId": "S3Bucket",
"message": "Bucket S3Bucket doesn't have encryption enabled",
"not-scored": false,
"pretty-risk-level": "High",
"provider": "aws",
"region": "us-east-1",
"resolution-page-url": "https://www.cloudconformity.com/knowledge-base/aws/S3/bucket-default-encryption.html",
"resource": "S3Bucket",
"risk-level": "HIGH",
"rule-title": "S3 Bucket Default Encryption",
"status": "FAILURE",
"tags": [
"Environment::ModernizationWorkshop"
],
"waste": 0
},
"id": "ccc:OrganisationId:S3-021:S3:us-east-1:S3Bucket",
"relationships": {
"account": {
"data": null
},
"rule": {
"data": {
"id": "S3-021",
"type": "rules"
}
}
},
"type": "checks"
},
{
"attributes": {
"categories": [
"security"
],
"compliances": [],
"cost": 0,
"descriptorType": "s3-bucket",
"extradata": [
{
"label": "LocationConstraint",
"name": "LocationConstraint",
"type": "META",
"value": "us-east-1"
}
],
"ignored": false,
"last-updated-date": null,
"logicalResourceId": "S3Bucket",
"message": "s3-bucket S3Bucket does not have S3 Block Public Access feature enabled.",
"not-scored": false,
"pretty-risk-level": "Very High",
"provider": "aws",
"region": "global",
"resolution-page-url": "https://www.cloudconformity.com/knowledge-base/aws/S3/bucket-public-access-block.html",
"resource": "S3Bucket",
"risk-level": "VERY_HIGH",
"rule-title": "Enable S3 Block Public Access for S3 Buckets",
"status": "FAILURE",
"tags": [
"Environment::ModernizationWorkshop"
],
"waste": 0
},
"id": "ccc:OrganisationId:S3-026:S3:global:S3Bucket",
"relationships": {
"account": {
"data": null
},
"rule": {
"data": {
"id": "S3-026",
"type": "rules"
}
}
},
"type": "checks"
}
]
CRITICAL: 3 offending entries found
11. You can see that you have three misconfigurations that are not meeting the minimum risk level that we defined as HIGH during the IaC pipeline creation. Keep in mind that you can change the risk level configuration anytime that you need.
For this case, we are going to do the fix direct in the CodeCommit where our CloudFormation template is, but in real life, you will be able to share the details above with your cloud architect team and DevOps engineers to improve the CloudFormation before pushing it to the code repository.
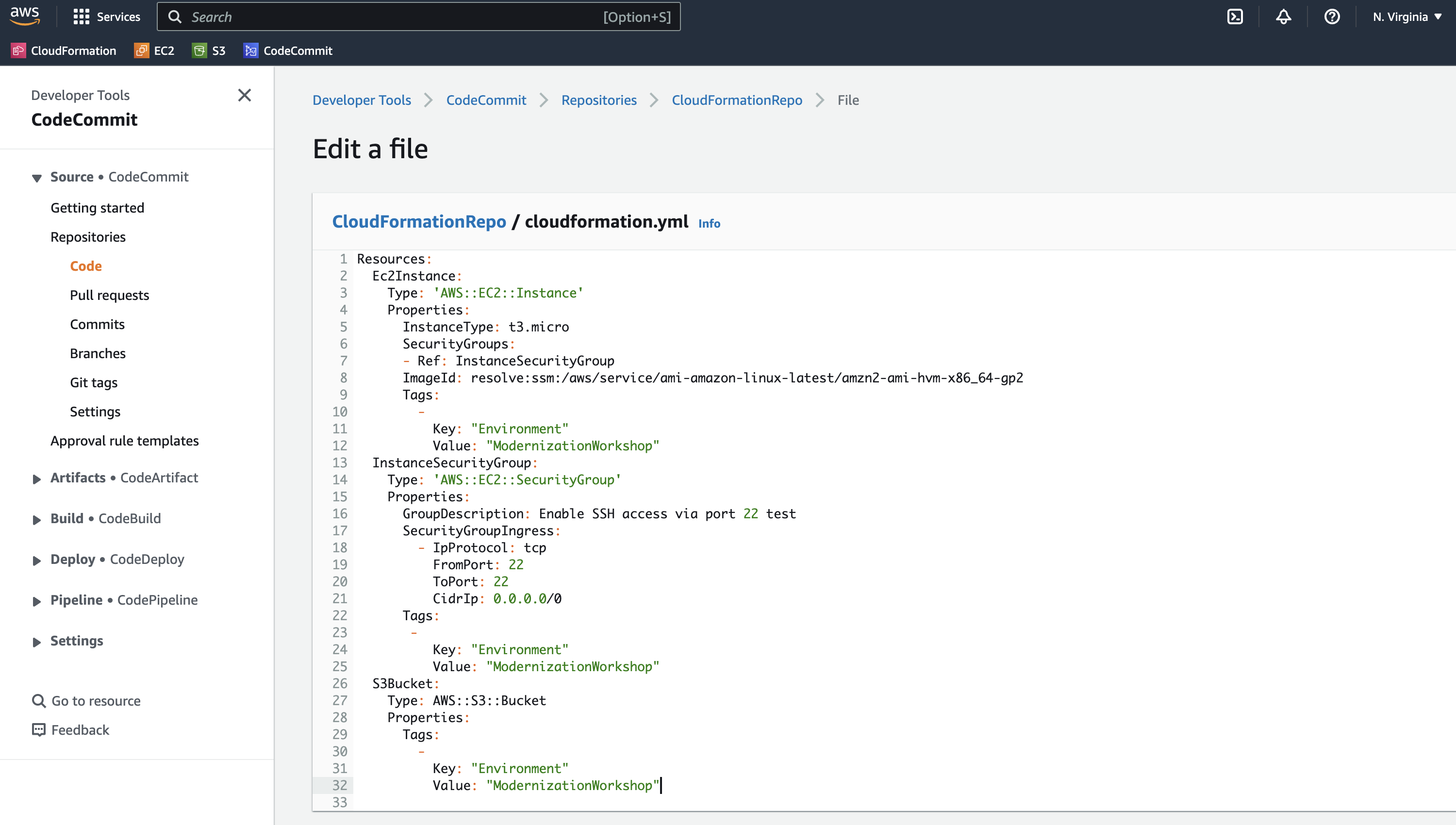
Let’s do the fixes in the CloudFormation then. 💻 Search for CodeCommit and then click the CloudFormationRepo that was created by the CloudFormation template earlier. Click on cloudformation.yml and then click Edit - you will see the following CloudFormation template for us to fix:
12. You will need to update the current CloudFormation template that you have with the new one that we updated below. This new CloudFormation has the goal to fix the two HIGH issues found by the Conformity Template Scanner.
The Image ID used is from us-east-1 in AWS. If you are using a different region to deploy the CloudFormation template, please use the proper Image ID from the region that you are using.
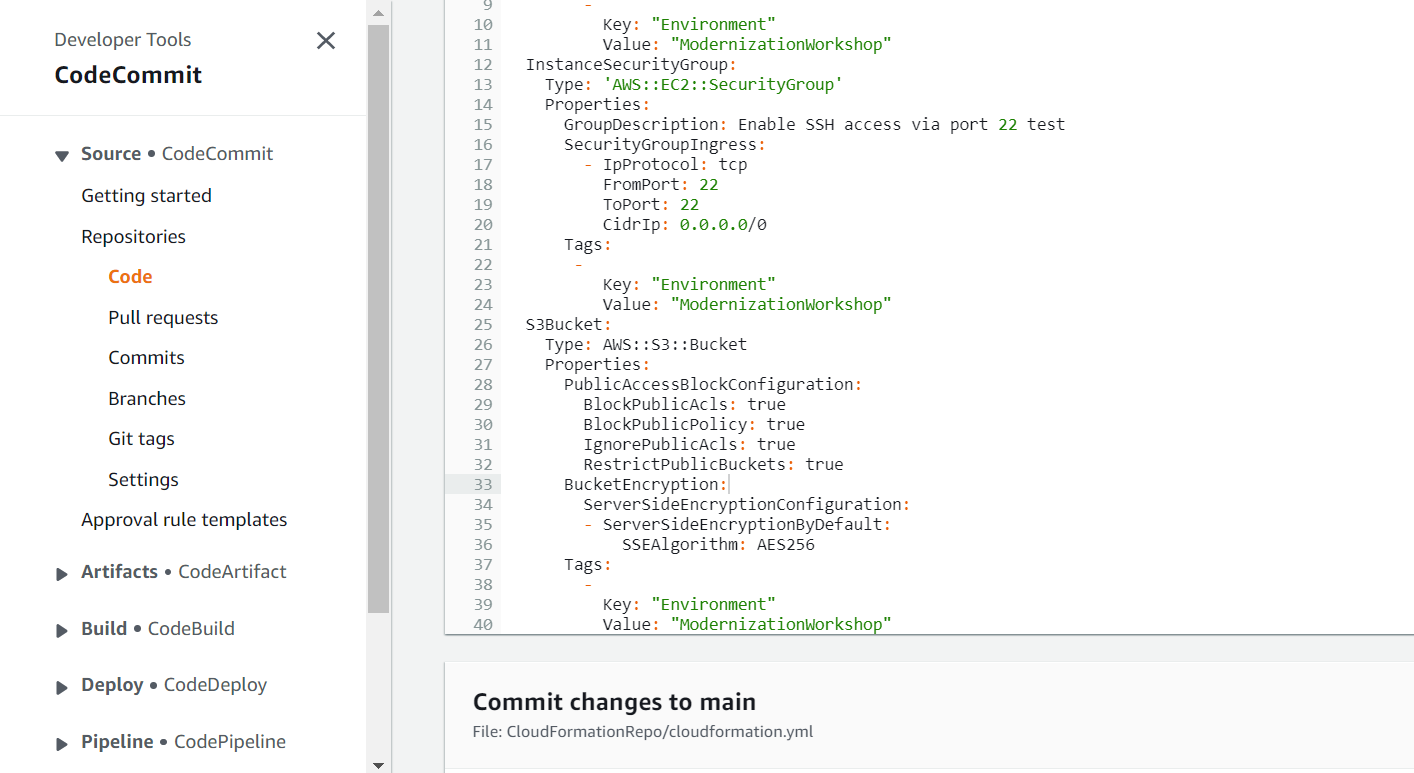
13. Copy and paste this new CloudFormation template in your environment:
Resources:
Ec2Instance:
Type: 'AWS::EC2::Instance'
Properties:
InstanceType: t3.micro
SecurityGroups:
- Ref: InstanceSecurityGroup
ImageId: resolve:ssm:/aws/service/ami-amazon-linux-latest/amzn2-ami-hvm-x86_64-gp2
Tags:
-
Key: "Environment"
Value: "ModernizationWorkshop"
InstanceSecurityGroup:
Type: 'AWS::EC2::SecurityGroup'
Properties:
GroupDescription: Enable SSH access via port 22 test
SecurityGroupIngress:
- IpProtocol: tcp
FromPort: 22
ToPort: 22
CidrIp: 0.0.0.0/0
Tags:
-
Key: "Environment"
Value: "ModernizationWorkshop"
S3Bucket:
Type: AWS::S3::Bucket
Properties:
PublicAccessBlockConfiguration:
BlockPublicAcls: true
BlockPublicPolicy: true
IgnorePublicAcls: true
RestrictPublicBuckets: true
BucketEncryption:
ServerSideEncryptionConfiguration:
- ServerSideEncryptionByDefault:
SSEAlgorithm: AES256
Tags:
-
Key: "Environment"
Value: "ModernizationWorkshop"
In the new CFT we added two configurations to fix the issue "BucketEncryption" and "PublicAccessBlockConfiguration".
14. Now you will just need to add the information requested for the commit and click in Commit Changes, this way the pipeline will kick-off automatically because of the changes happening:
15. Go to Pipelines on the left under CodePipeline and select the ModernizationWorkshop pipeline to see the stages:
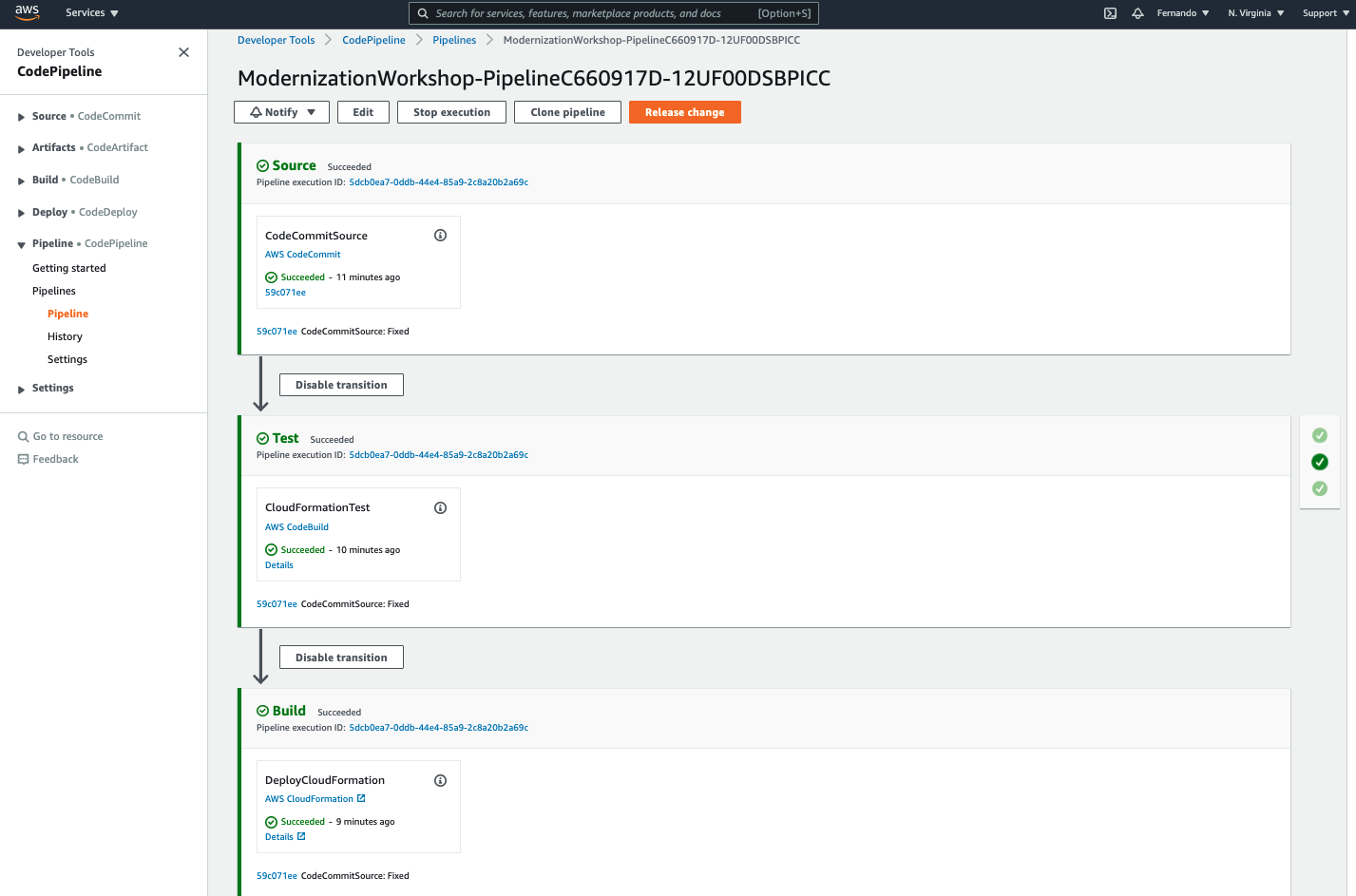
16. Now, you will see that the CloudFormation template passed in the Template Scanner analysis and it was able to be built in AWS 🚀 Congratulations, you have a simple, fully automated IaC with security scanning for your Cloud Formation templates before building the infrastructure.
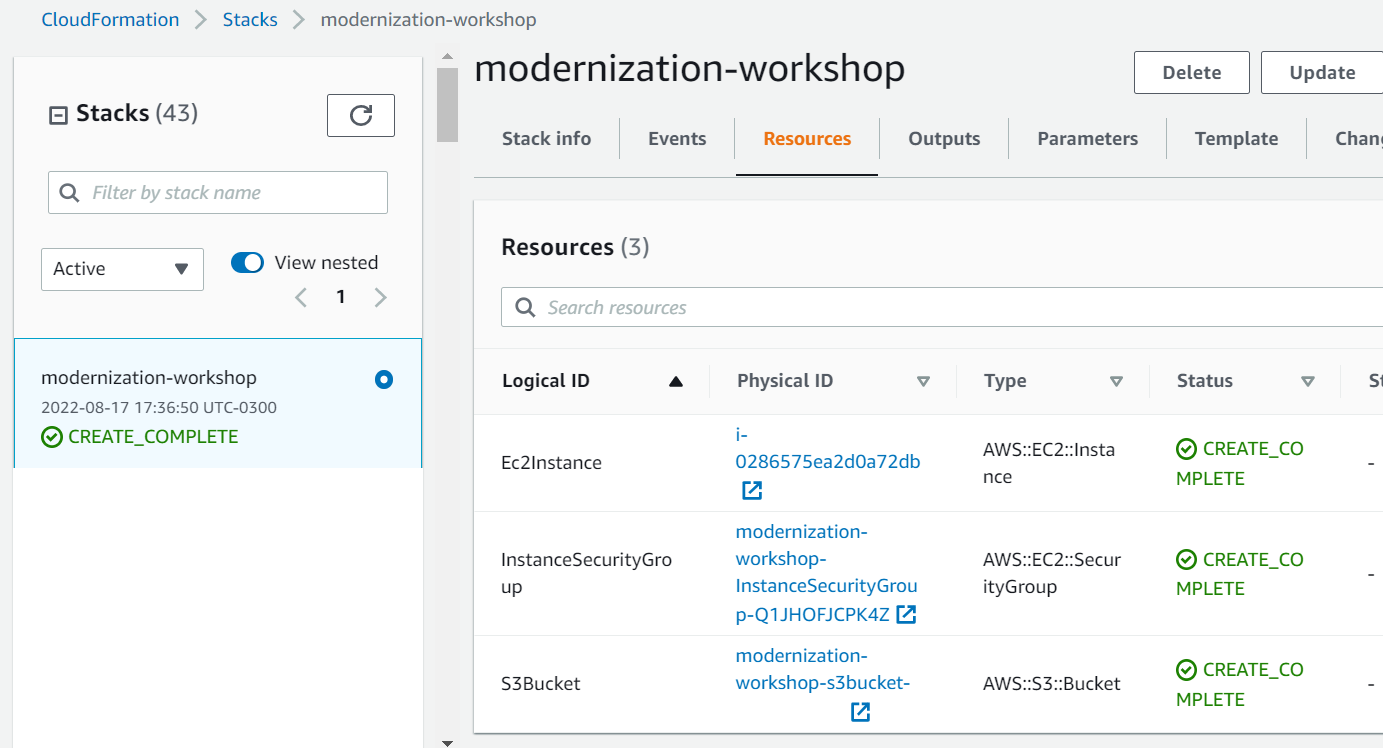
The CloudFormation template will be creating a Amazon S3 bucket, a security group, and an Amazon Elastic Compute Cloud (EC2). You can go to the CloudFormation stack and delete the stack that we just created: modernization-workshop-cft-example
If you are using your own account, remember to delete the CloudFormation created with the name modernization-workshop-cft-example for you don't spend unnecessary money.
Now, you can skip to the Lab 5. Integrating AWS with Cloud One - Conformity 💻 🚀