Finding and Remediating Misconfigurations
Use cases of possible cloud misconfiguration and how to fix it
We have prepared a CloudFormation template with some common use cases of misconfiguration for main AWS services that we see in many customers. This way you will be able to run the template in your own AWS account for some practice, or you could deploy the template in an AWS account provided for a lab purpose at a Security Immersion Day event. Here are some the use cases that we created for you:
-
Amazon S3 Bucket
- Amazon S3 Bucket Publix Access Via Policy
- Amazon S3 Server Side Encryption
-
AWS Identity and Access Management (IAM)
- Overly Permissive IAM Role
-
Amazon Simple Queue Service (SQS) and Amazon Simple Notification Service (SNS)
- Unencrypted SQS queue
- SNS Topics Disable
⚠️ For the these labs above you will need to deploy this CloudFormation stack, below:
or
You can get the CloudFormation Template for the labs using this Link
Populating the AWS account with misconfigurations for the labs
-
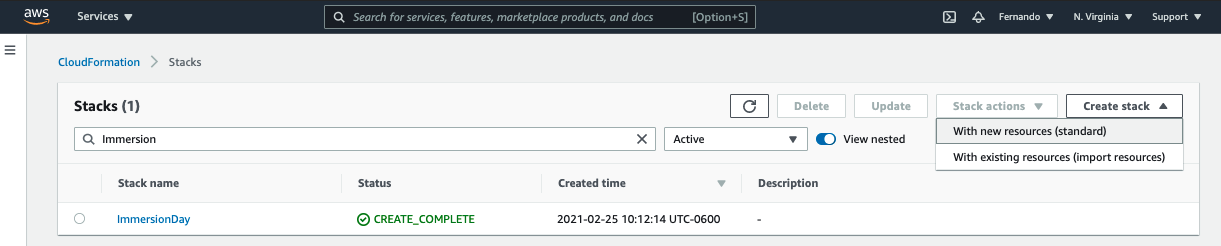
Back in your AWS account, go to the AWS Cloud Formation console
-
Select Create stack and then With new resources from the drop-down menu
-
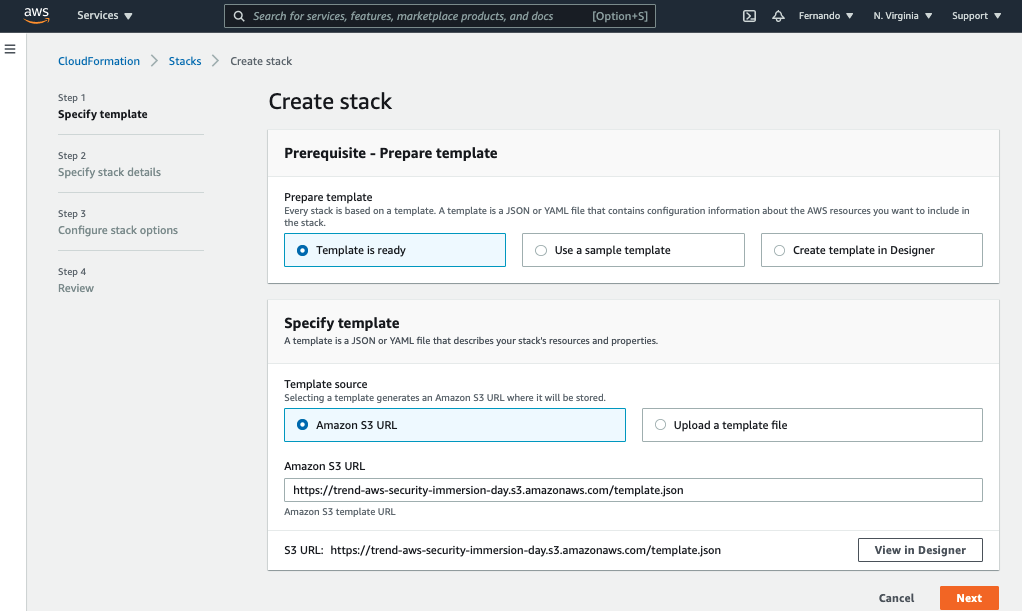
Use the above CloudFormation template link to create the stack in the AWS account.
-
Paste the link into Amazon S3 URL field and click Next:
-
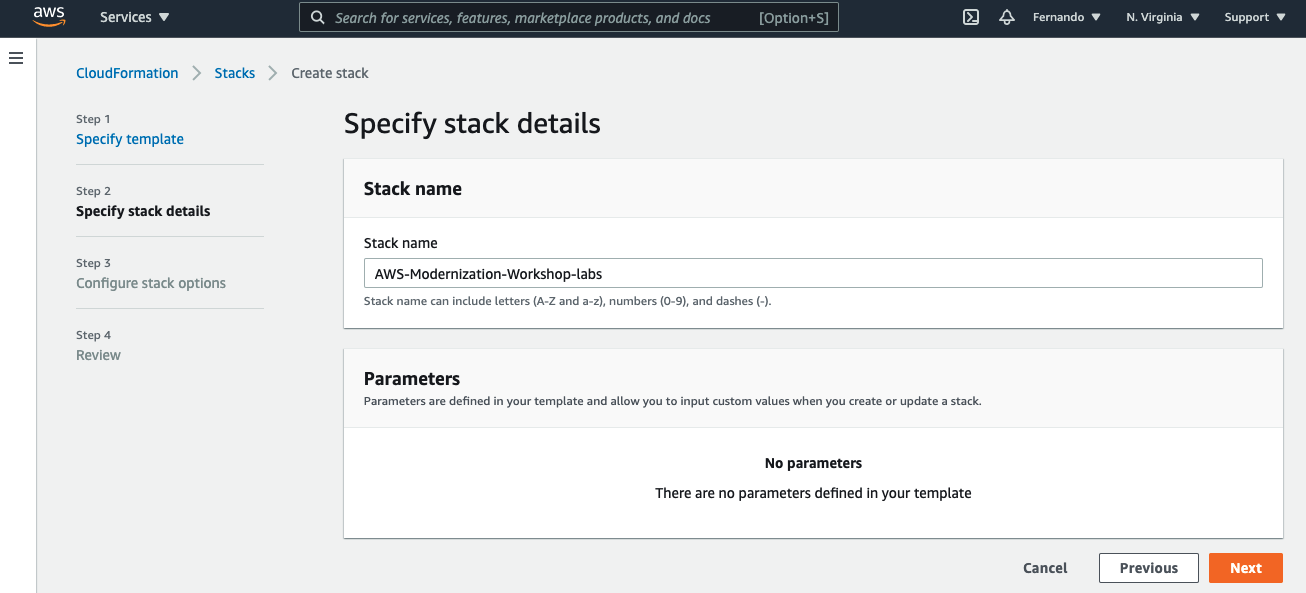
Set up the name of the CloudFormation stack as AWS-Modernization-Workshop-labs
-
Click Next
-
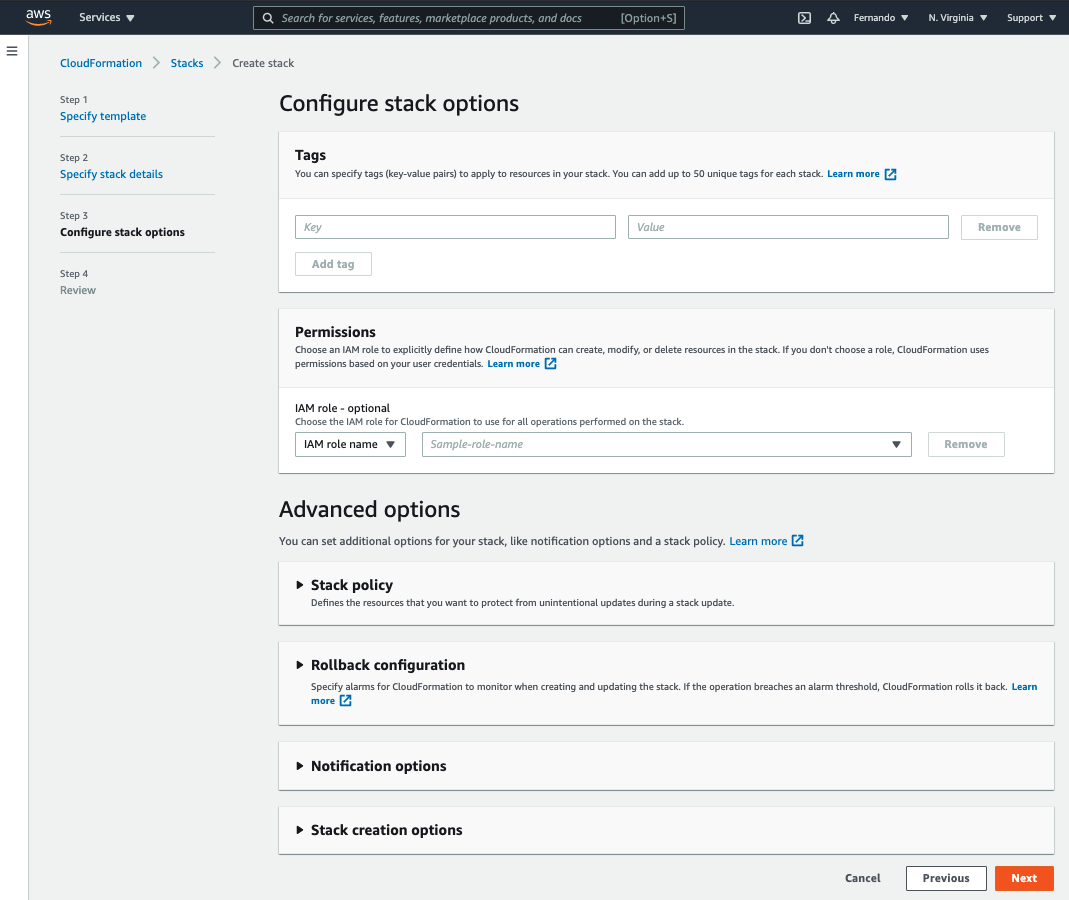
Scroll down, check the box to acknowledge and then click Create stack
-
After a couple of minutes, the stack will be completed, and you will be able to start the labs
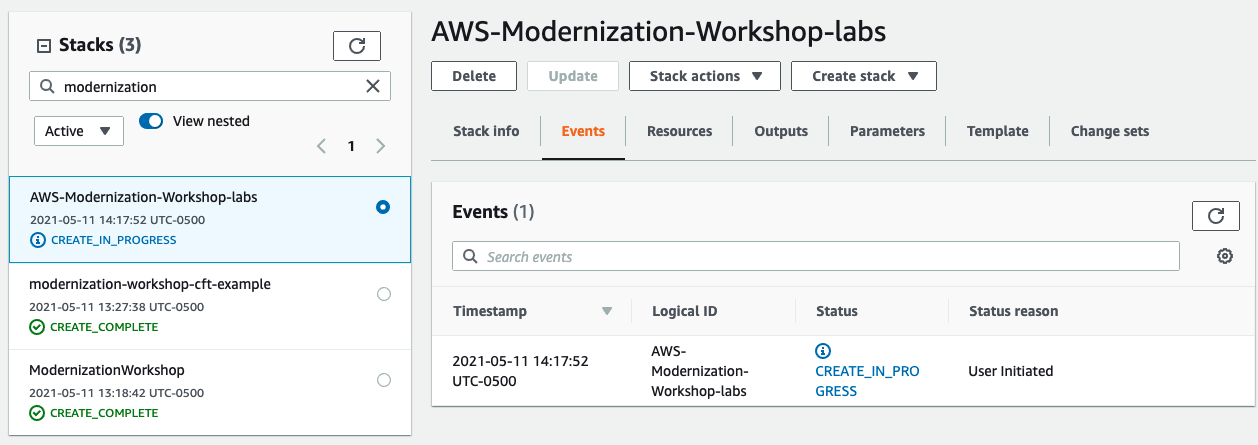
Because we are not using the Realtime monitoring in Cloud One - Conformity in this lab will be important to manually force a Conformity check scan to recognize all the new resource created from the CloudFormation template. If not it will take a couple of minutes to run the hourly Conformity check.
Force Run Conformity Bot
- Log in Cloud One account, select Conformity, select your AWS account on the left side, and then click on Run Conformity Bot. It will force a full Conformity check in your AWS account.

Extra Lab - Scanning CloudFormation Template with some misconfigurations
- Scanning IaC CloudFormation template and fixing it
- Enable Amazon S3 Block Public Access for Amazon S3 buckets
- Amazon S3 Bucket Default Encryption
- Amazon S3 Bucket Logging Enabled
- VPC Flow Logs Enabled
⚠️ For the template scanner you will need to download this CloudFormation template to use in your IDE for the exercise -> LINK
⚠️ This is a great challenge for you to learn more about how to see misconfigurations in the early stage of the IaC pipeline with our IDE Security Plugin.
Let’s start remediating the misconfiguration issues in the AWS Account. 💻
