Amazon S3 - lab
Scenario
In this scenario we have a use case where a customer accidentally created a bucket and made it public without encryption. Our goal here is to detect the bucket and fix its two main configuration security issues.

Automatically Finding the Misconfiguration
It's very important you completed chapter 5 of the workshop before starting this one, because you will need a Trend Micro Cloud One account that is integrated with your AWS account.
We will use the Confomirty dashboard to search for the misconfigurations.
1. Log in to Trend Micro - Cloud One, select Conformity, select the account on your left that you have integrated for this workshop, and then click on “Browse All Checks”

2. Click Filter checks to open the filter options so we can enable an easy way to investigate some checks for Amazon S3 buckets.
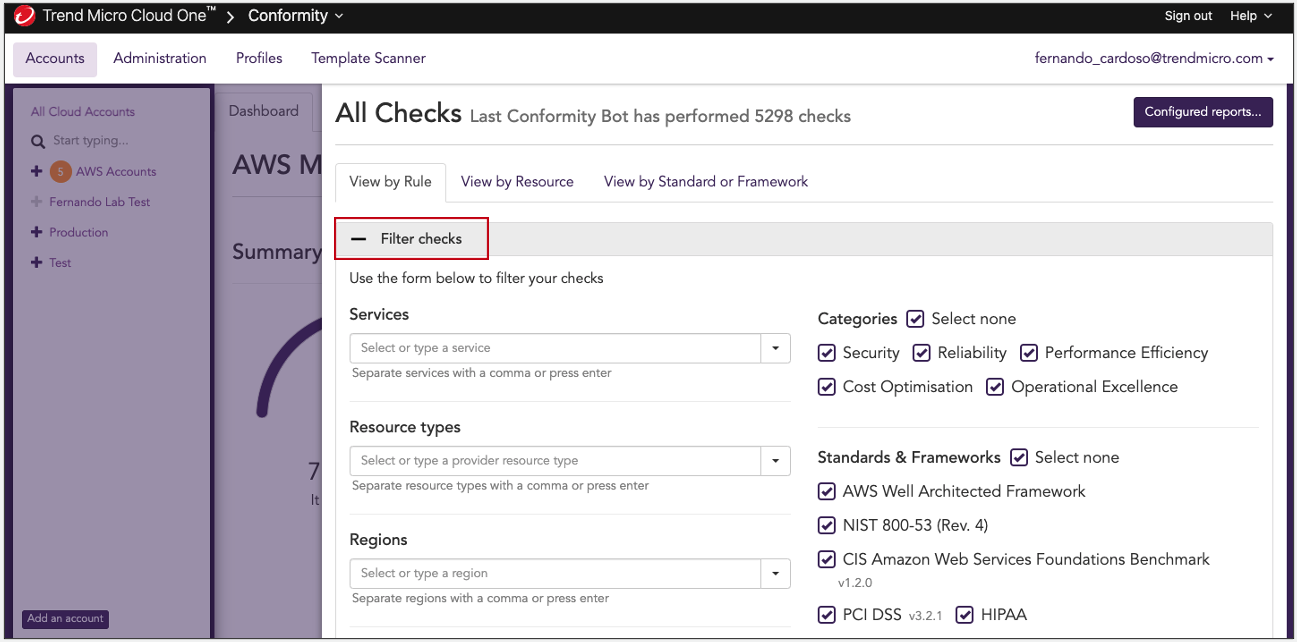
3. Define the Filter check
Here are the configurations that you should apply:
- On Resource Types, search for S3 Bucket and press Enter
- On Search Tags, add Lab::2 and press Enter
- On Status, uncheck Success
After you complete the configurations, click Filter Check again

If after applying the filter Tag the resource are not showing, it's because you need to force a Run Conformity Bot in the main dashboard as described here Run Conformity Bot
4. How to look for the specific Conformity check to properly perform remediation
Locate the two Conformity checks that pertain to the misconfigurations of this scenario (S3 Bucket Public Access Via Policy and Server Side Encryption). Next to each, select Resolve, which will populate the step-by-step instructions for remediating these misconfigurations.

5. View more details about the the Conformity checks
Selecting the Conformity checks will allow you to see more details about the misconfiguration that was found. You will also have the direct link to the resource to help you to review and fix the misconfigurations that have been found.

6. Remediation
Click Resolve to bring you to the Knowledge Base, here you will find the step-by-step on how to remediate the misconfiguration found by Conformity.
- S3 Bucket Public Access Via Policy - Knowledge Base Link
- Server Side Encryption - Knowledge Base Link

7. Review the remediation
After completing the remediation for these two use cases, you can return to the Conformity dashboard and click Run Conformity Bot to start a new process.
The default Conformity process for monitoring is hourly checks performed by the Conformity bot. You can also manually run the checks, or enable the real-time monitoring feature.
After couple minutes the Conformity Bot check will finish and you can check if the previous configurations will now appear as Succeeded instead of Failed.
